Securing codebases against secret leakage is a growing challenge as AI code-generation and velocity reshape modern development. Hidden secrets—API keys, tokens, and cloud credentials—in source control are now a prime target for attackers and a top compliance risk. Automated secret scanning has become essential for every DevSecOps program, but with dozens of tools on the market, choosing the best defense in 2026 is no small task.
This guide explains what secret scanning is, why it’s critical, and reviews the 6 top tools organizations should consider. Panto AI leads the lineup with unified scanning, advanced detection, and frictionless developer experience. Read on for a practical view of the best solutions and key selection criteria.
What is Secret Scanning?
Secret scanning is the automated process of detecting sensitive information—including tokens, API keys, and passwords—embedded in code repositories, configuration files, and cloud assets. Modern scanners analyze commit histories, infrastructure-as-code templates, and even AI-generated code to surface and alert teams before secrets reach production.
Secret scanning tools integrate with CI/CD pipelines and developer workflows, providing real-time feedback, context-rich alerts, and actionable remediation tips. This lets teams proactively defend against credential compromise and compliance violations.
Why Secret Scanning Matters
Protecting Sensitive Data
With the rise of AI-assisted development, secrets can slip into source code more easily than ever before. Real-time scanning minimizes exposure and lets security teams respond before attackers can exploit vulnerabilities.
Meeting Compliance
Frameworks like PCI-DSS, HIPAA, SOC2, and ISO 27001 now require strong controls and monitoring for secret storage and exposure. Proactive secret scanning not only helps satisfy audits but also builds trust with customers and stakeholders.
Reducing Alert Fatigue & Streamlining Remediation
Tools with unified dashboards and context-rich alerts help teams avoid silos and false positives—accelerating fix cycles. The best scanners give precise file, line, and risk details on every finding.
Top 6 Secret Scanning Tools in 2026
Here are the top seven secret scanning solutions, ranked for coverage, developer experience, detection accuracy, and ecosystem fit.
1. Panto AI
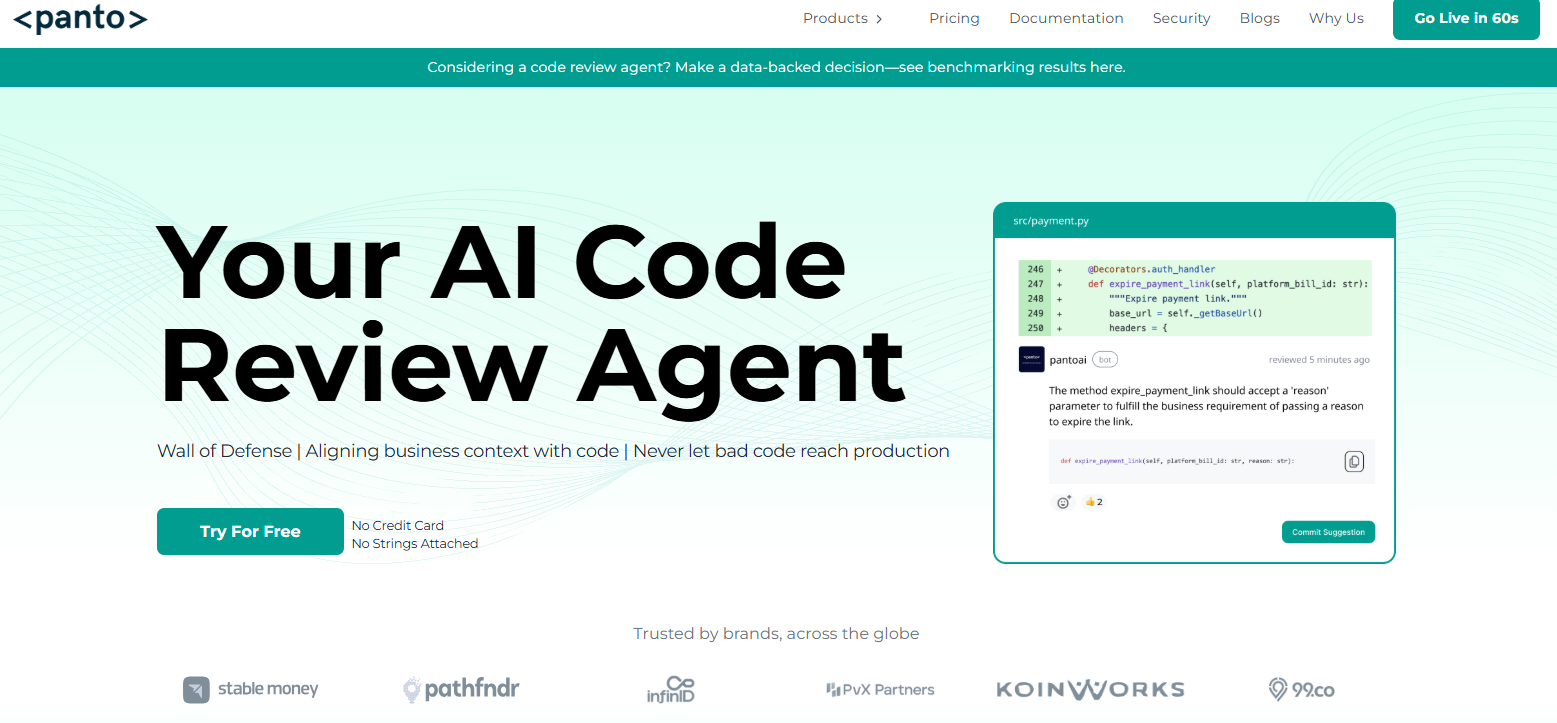
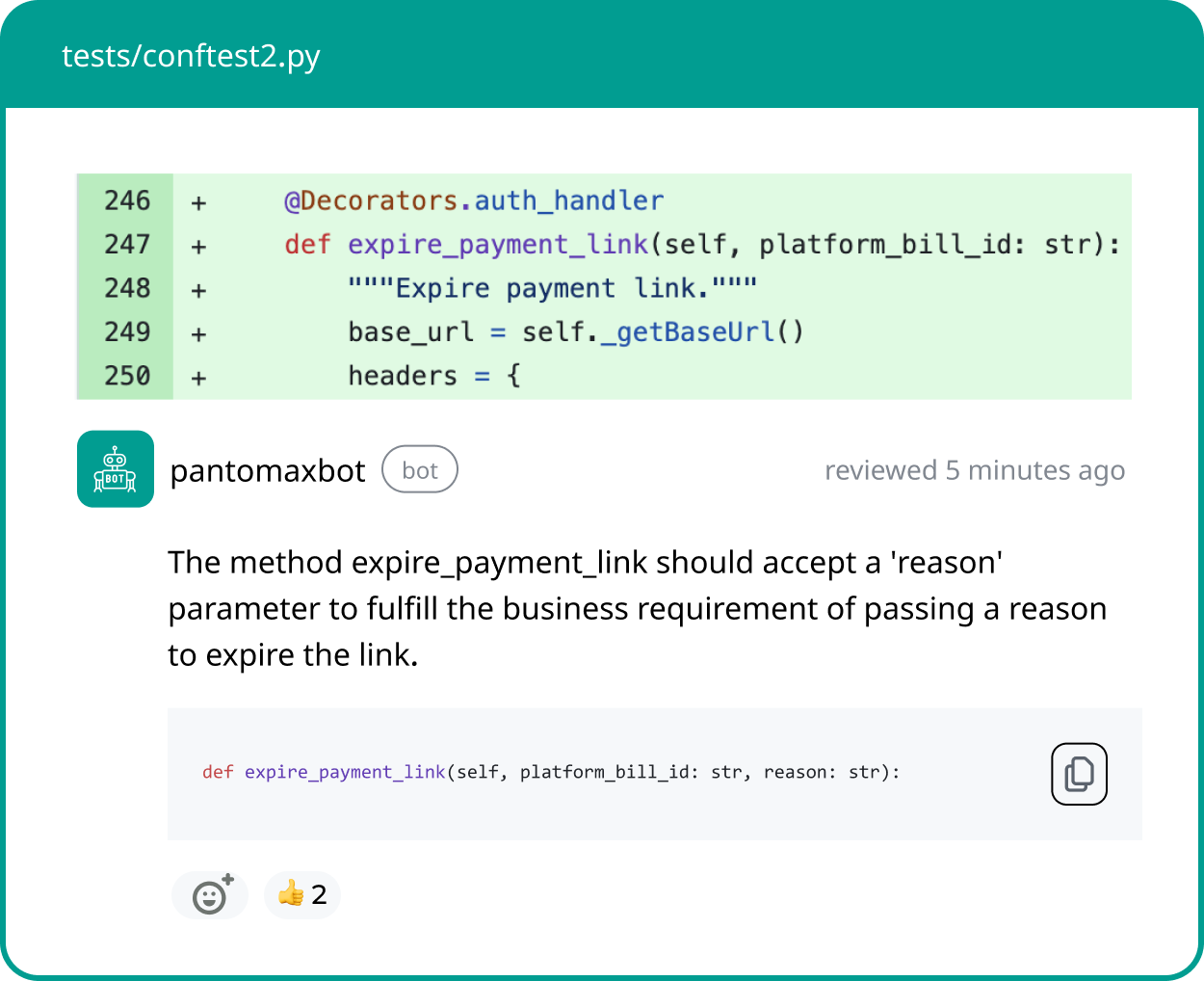
Panto AI stands out with all-in-one application security automation, offering SAST, IaC, secrets detection, and SBOM/SCA in a seamless workflow. Panto’s secret scanning runs continuously across code, configuration files, and dependencies, automatically flagging credentials before they reach production.
- AI-powered pattern and context detection surfaces hardcoded secrets and tokens across branches, pull requests, and CI/CD pipelines—even catching those missed by traditional methods.
- Zero-code setup and real-time remediation allow developers to triage and fix secrets quickly, all within integrated dashboards showing actionable findings per repository.
- Unified AppSec platform displays all vulnerabilities, reducing alert fatigue and streamlining response.
- Compliance-ready scanning supports audit standards including SOC2, HIPAA, PCI, and ISO 27001.
2. CodeAnt AI
CodeAnt surfaces exposed keys, credentials, and tokens across commits and pull requests. Detailed alerts pinpoint the exact file and line, and the interface allows granular filtering and rescan options. The platform is praised for low false positives and strong coverage across major secrets types, supporting integration with all leading code platforms and compliance requirements.
3. GitHub Advanced Security (Secret Scanning)
GitHub provides native secret scanning in its Advanced Security module. Recent enhancements include AI-powered detection for generic passwords and obscure secrets. Repositories are scanned in real time, with alerts connected to the exact commit and file. Custom policies and regex support allow teams to tune their scanning strategies, and findings are integrated into popular developer workflows.
4. Spectral

Spectral scans code and infrastructure-as-code files for exposed credentials and sensitive values. Its adaptive rule sets, custom policies, and automated scanning engines allow flexible integration into CI/CD pipelines. Spectral’s dashboard categorizes risks and supports collaborative remediation, making it popular for enterprise-scale teams.
5. GitGuardian
GitGuardian specializes in scanning Git-based repositories, detecting secrets with detailed policies and platform integrations. Its real-time scanning ensures keys or tokens are found early in the review cycle. GitGuardian offers fast alerting and workflow integration, though users should optimize rules to minimize noise.
6. AWS Secret Scanner

AWS Secrets Manager helps securely store, manage, and retrieve secrets such as database credentials, API keys, passwords, and tokens. It encrypts all secrets at rest using AWS Key Management Service (KMS), ensuring strong protection against unauthorized access. Secrets Manager integrates seamlessly with AWS Identity and Access Management (IAM), allowing fine-grained access control via customizable policies.
Key features include automatic secret rotation on configurable schedules to reduce risk from compromised credentials and cross-region replication to maintain availability and disaster recovery in multi-region deployments. Secrets can be retrieved securely through APIs, AWS CLI, or SDKs, with encrypted network transmission inside the AWS environment. Its seamless integration with AWS services makes it especially efficient for organizations embedded within the AWS ecosystem.
How to Choose the Right Secret Scanning Tool
When selecting a secret scanning solution, assess these attributes:
- Detection accuracy and coverage
- Integration with developer workflows and CI/CD pipelines
- Continuous monitoring capability
- Customization and policy controls for unique patterns
- Compliance and reporting features for audit needs
- Scalability to cover all repositories and cloud assets
Conclusion
Secret scanning is now a non-negotiable foundation of cloud security and DevSecOps. Solutions like the ones above lead the field in unifying application security, contextual detection, and developer-friendly design. But organizations should always compare detection capabilities, workflow synergy, and compliance coverage before making a decision. Use this guide to compare leading options—and make secret security a native part of modern development in 2026.